Search results for tag #security
Good CCC talk - Escaping Containment: A Security Analysis of FreeBSD Jails: https://media.ccc.de/v/39c3-escaping-containment-a-security-analysis-of-freebsd-jails#t=247 #security
The situations way more complex than just a "debate". Psilocybin clearly has benefits for mental health treatment - but taking it off class A schedule 1 creates obvious #security risks of #diversion - especially with the #NHS being on the ropes and a lot of disgruntled staff with low morale.
There have also already been quite a few private #pharmacists nicked and struck off for diversion and/or loose prescription of other #ControlledDrugs
This needs to be addressed before any change to #drugs laws (or even if they do happen, healthcare professionals are going to be too wary of prescribing the stuff anyway for fear of making a career-limiting move or even getting in legal trouble), this is already affecting #ADHD patients who could benefit from #amfetamines
Friends, at the end of a horrible year, please let's talk about something *nice*.
My EUR 0.02: You Have Installed OpenBSD. Now For The Daily Tasks. https://nxdomain.no/~peter/openbsd_installed_now_for_the_daily_tasks.html (tracked https://bsdly.blogspot.com/2024/09/you-have-installed-openbsd-now-for.html)
Bonus track: Yes, The Book of PF, 4th Edition Is Coming Soon https://nxdomain.no/~peter/yes_the_book_of_pf_4th_ed_is_coming.html (tracked https://bsdly.blogspot.com/2025/07/yes-book-of-pf-4th-edition-is-coming.html)
#freesoftware #openbsd #freebsd #bookofpf #networking #security #deveops #development #sysadmin @nostarch
#SECURITY GUARANTEES INCLUDE U.S. MILITARY PRESENCE IN #UKRAINE: For the first time since Russia's full-scale invasion of Ukraine, the U.S. included the deployment of American troops in Ukraine in security guarantees. https://www.ukrinform.ua/rubric-polytics/4075052-ssa-mozut-rozgornuti-vijska-v-ukraini-ak-element-garantij-bezpeki-tusk.html
Not sure I believe #Trump wil follow through…
#US offers #Ukraine 15-year #security guarantee as part of peace plan, #Zelensky says
The #UnitedStates is offering Ukraine security guarantees for a period of 15 years as part of a proposed peace plan, Ukrainian President Volodymyr Zelensky said Monday, though he said he would prefer an American commitment of up to 50 years to deter #Russia from further attempts to seize its neighbor’s land by force.
#PutinsPuppet
https://apnews.com/article/russia-ukraine-war-trump-zelenskyy-peace-b784a9af1803995bfb7152eceb5477f1
GrapheneOS version 2025122500 released:
https://grapheneos.org/releases#2025122500
See the linked release notes for a summary of the improvements over the previous release.
Forum discussion thread:
https://discuss.grapheneos.org/d/29501-grapheneos-version-2025122500-released
Inside #Uzbekistan 's nationwide license plate #surveillance system | TechCrunch
We know this because the country’s sprawling license plate-tracking surveillance system has been left #exposed to the internet.
#Security researcher Anurag Sen, who discovered the security lapse, found the license plate surveillance system exposed online without a #password , allowing anyone access to the data within. It’s not clear how long the system has been public
#alpr #privacy
https://techcrunch.com/2025/12/23/inside-uzbekistans-nationwide-license-plate-surveillance-system/
It bugs me every time someone non-technical, from a completely different line of work, says you no longer need to learn to code because you can "build" an app, website, or server in minutes with AI. Nobody performs chiropractic neck manipulations based on AI tips, nobody does professional construction work, or performs surgery with AI... right? (At least, I hope not.) And people usually understand that. So why can't they grasp that you still need to be a professional and actually know what you're doing, with or without an AI? You wouldn't tell a friend to "just do it" when they a) have no idea what you’re asking, and b) don't know how to do it.
Every line of code is a liability. It's a dangerous world right now, with people mindlessly throwing more and more junk online. Everyone will get hacked eventually.
#AI #ArtificialIntelligence #Coding #Programming #WebDev #Security
What to do with TOTP MFA credentials these days? I currently do #1, but it adds complexity. I've seen some recommends for #2, which surprises me a bit. But then again a password manager failure is like catastrophic either way. Also if I think about it, based on the logic of option 1, I shouldn't have the recovery codes in the pw manager db either.
| Store them in another app/password manager (synced): | 11 |
| Store them in your password manager next to your passwords: | 16 |
| Store them in another app (not-synced): | 4 |
I just realised a behavior that pervasive #security code scanning induces in me. We have a big, shared corporate repo for all company code. We've begun doing really aggressive, continuous scanning and cutting tickets to people on vulnerable code, even if it's not in production or in use.
I get it. I understand why. But the behavior it drives in me is that I won't commit anything to the company repo unless (a) I think it's basically perfect, and (b) I'm willing to deal with all the noise if it's not.
Scratchpads? Work in progress? prototypes? Not if there's a chance a robot is going to nag the shit out of me for every mistake. Those can just live on my laptop harddrive now, which is not where the business probably wants them.
This season reminds me of a time when I was doing #cybersecurity for a financial firm in London. The firm goes into "code freeze" in the first or second week of December until January to minimize the possibility of problems during the holidays.
I was doing #security architecture analysis on an important system. Basically the US SEC had demanded they start using a purpose-built system to track certain numbers (I'll explain in a reply to this) instead of just emailing spreadsheets around. So they had basically built a system that was a spreadsheet in a website. They had one year to comply. This system had not yet launched. If it didn't go live in this last possible week, they'd have to explain to the SEC how, 12 months on, they had failed to deploy anything at all in response to the requirement. (I'm sure I'm being imprecise here, that's the gist of it)
1/
Node.js devs, so picture this: you run `npm install` and you get a bunch of packages with audit errors.
The only thing I want to know at that point is what’s the root package that these dependencies belong to? (Running npm audit fix is a last resort as I don’t like it fiddling around with the dependencies of nested packages.)
It’s also not a straightforward thing to do, but it’s nothing jq and a bit of piping can’t fix:
```bash
npm audit --json | jq -r '.vulnerabilities[].name' | xargs -n1 npm ls
```
If you’re using fish shell, add an abbr(aviation) or an alias to that with a name like npm-audit-tree and you’re golden ;)
```bash
abbr --add --global npm-audit-tree 'npm audit --json | jq -r '.vulnerabilities[].name' | xargs -n1 npm ls'
```
(I usually prefer abbreviations to aliases as I like to remember/see the actual command being executed.)
Enjoy 💕
#NodeJS #npm #audit #security #JavaScript #JSON #jq #xargs #dev #tip
Interesting links of the week:
Strategy:
* https://assets.publishing.service.gov.uk/media/69411a3eadb5707d9f33d7e8/E03512978_-_Un-Act_The_National_Security_Act_in_2024_Accessible.pdf - the UK tries to define what a state threat is (and includes everyone from professional spies to someone who may not even know they pose a risk)
Standards:
* https://csrc.nist.gov/pubs/sp/800/82/r3/final - courtesy of @Secure_ICS_OT
Threats:
* https://www.microsoft.com/en-us/security/security-insider/threat-landscape/microsoft-digital-defense-report-2025 - MSFT's take on the landscape
Detection:
* https://ip.thc.org/ - @thc don't do things by half... here's a very large IP/DNS database
* https://www.fortinet.com/blog/threat-research/uncovering-hidden-forensic-evidence-in-windows-mystery-of-autologger - Fortinet look at alternate DFIR sources for Windows
* https://troopers.de/downloads/troopers19/TROOPERS19_DM_Threat_Modelling_Cisco_ACI.pdf - surprisingly, I have my own take on ACI, but here's one from @ERNW
Bugs:
* https://kqx.io/post/qemu-nday/ - popping Qemu like it was 13 years ago
* https://www.freebsd.org/security/advisories/FreeBSD-SA-25:12.rtsold.asc - FreeBSD AV:A oopsie
* https://projectzero.google/2025/12/android-itw-dng.html - GOOG discuss a nasty image
Exploitation:
* https://hackers-arise.com/sdr-signals-intelligence-for-hackers-building-a-low-cost-private-4g-lte-network/ - ever wanted your own 4G LTE playground?
* https://podalirius.net/en/mainframe/as400-forensics-retrieving-your-licence-keys-from-disk-images/ - getting the keys to the museum
* https://caido.io/ - another alternative to Burp, with a focus on multi-stage attacks
* https://arxiv.org/pdf/2512.09882 - AI vs flesh face off
Hard hacks:
* https://blog.quarkslab.com/modern-tale-blinkenlights.html - @quarkslab pays €12 for a good time
Hardening:
* https://ariadne.space/2025/12/12/rethinking-sudo-with-object-capabilities.html - @ariadne discusses their sudo alternative
* https://lpc.events/event/19/contributions/2159/attachments/1833/3929/BpfJailer%20LPC%202025.pdf - building jails with eBPF
* https://pages.nist.gov/OSCAL/ - an as-code approach to standardised standards
Remote code execution via ND6 Router Advertisements https://lobste.rs/s/l6nsa1 #freebsd #security
https://www.freebsd.org/security/advisories/FreeBSD-SA-25:12.rtsold.asc
Encryption isn't hostile. It's a bedrock of our cybersecurity 🔐
The UK's national security laws join a long line of attempts to frame encrypted messaging as something to be broken into pieces.
Without it, we're more open to threats from hackers and criminals.
#e2ee #encryption #privacy #cybersecurity #nationalsecurity #security #ukpolitics #ukpol
GrapheneOS version 2025121700 released:
https://grapheneos.org/releases#2025121700
See the linked release notes for a summary of the improvements over the previous release.
Forum discussion thread:
https://discuss.grapheneos.org/d/29166-grapheneos-version-2025121700-released
🧵 Tech-themed works, 26/x
Black Hat hacker (2016)
#hacker #malware #cybercrime #cybersecurity #InfoSec #security #safety #LowPoly #CharacterDesign #design #artwork #sculpture #3DArt #3DModeling #3DArtist #illustration #illustrator #picture #digital #style #art #artist #arts #arte #designer #GraphicDesign #3D #3DRendering #CGI #Blender3D #B3D #blender #DigitalArt #ArtLovers #MastoArt #FediArt #MastodonArt #CreativeToots #ArtistsOnMastodon
Just updated Node Pebble to support latest release version of Let’s Encrypt’s Pebble testing server.
https://codeberg.org/small-tech/node-pebble
Enjoy!
💕
#LetsEncrypt #Pebble #testing #tls #ssl #security #NodeJS #JavaScript
I have some problems about the contemporary push to adopt passkeys everywhere. They're perhaps only half-baked, but I wrote them up anyway.
I never thought I'd become a technical conservative, but I guess spending the best part of a decade as a reliability engineer has taught me to see opportunities for stuff to break.
https://www.arcanalabs.ca/essays/tech/2025/12/16/passkey-problems.html
#Zelensky said on Sunday that the #US, #Europe & other partners' #security guarantees instead of #NATO membership were a compromise on #Ukraine's side.
"From the very beginning, Ukraine's desire was to join NATO, these are real security guarantees. Some partners from the US & Europe did not support this direction," he said in answer to questions from reporters in a WhatsApp chat.
"Thus, today, bilateral #security guarantees between #Ukraine & the #US, Article 5-like guarantees for us from the US, & security guarantees from European colleagues, as well as other countries — #Canada, #Japan — are an opportunity to prevent another Russian invasion," #Zelensky said.
"And it is already a compromise from our part," he said, adding that the security guarantees should be legally binding.
ACME Device Attestation Extension https://lobste.rs/s/ues4u6 #security
https://datatracker.ietf.org/doc/draft-ietf-acme-device-attest/
The story of Propolice, the OpenBSD stack protector https://www.undeadly.org/cgi?action=article;sid=20251212094310 #openbsd #propolice #stackprotection #security #securecode #exploitmitigation #secureprogramming
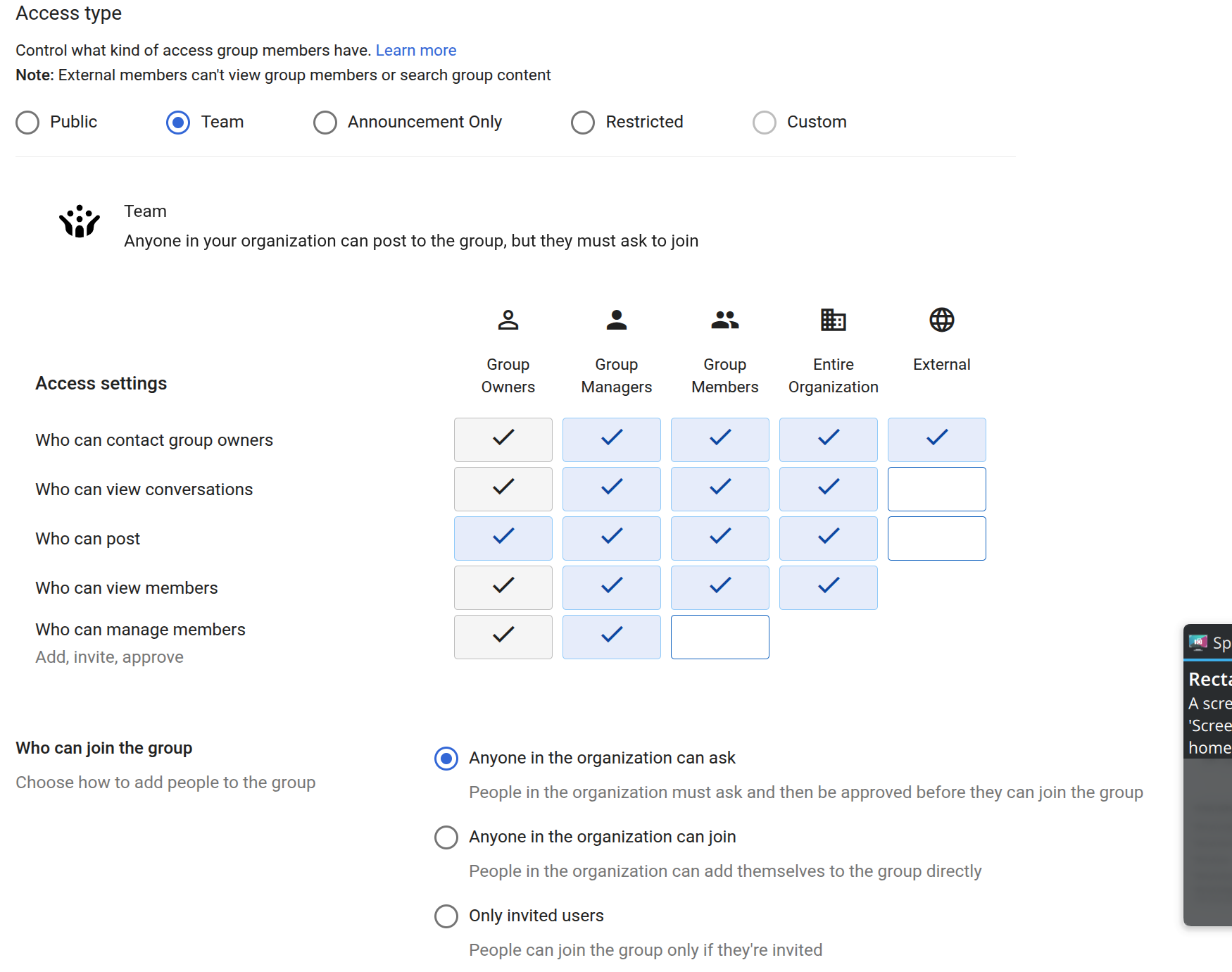
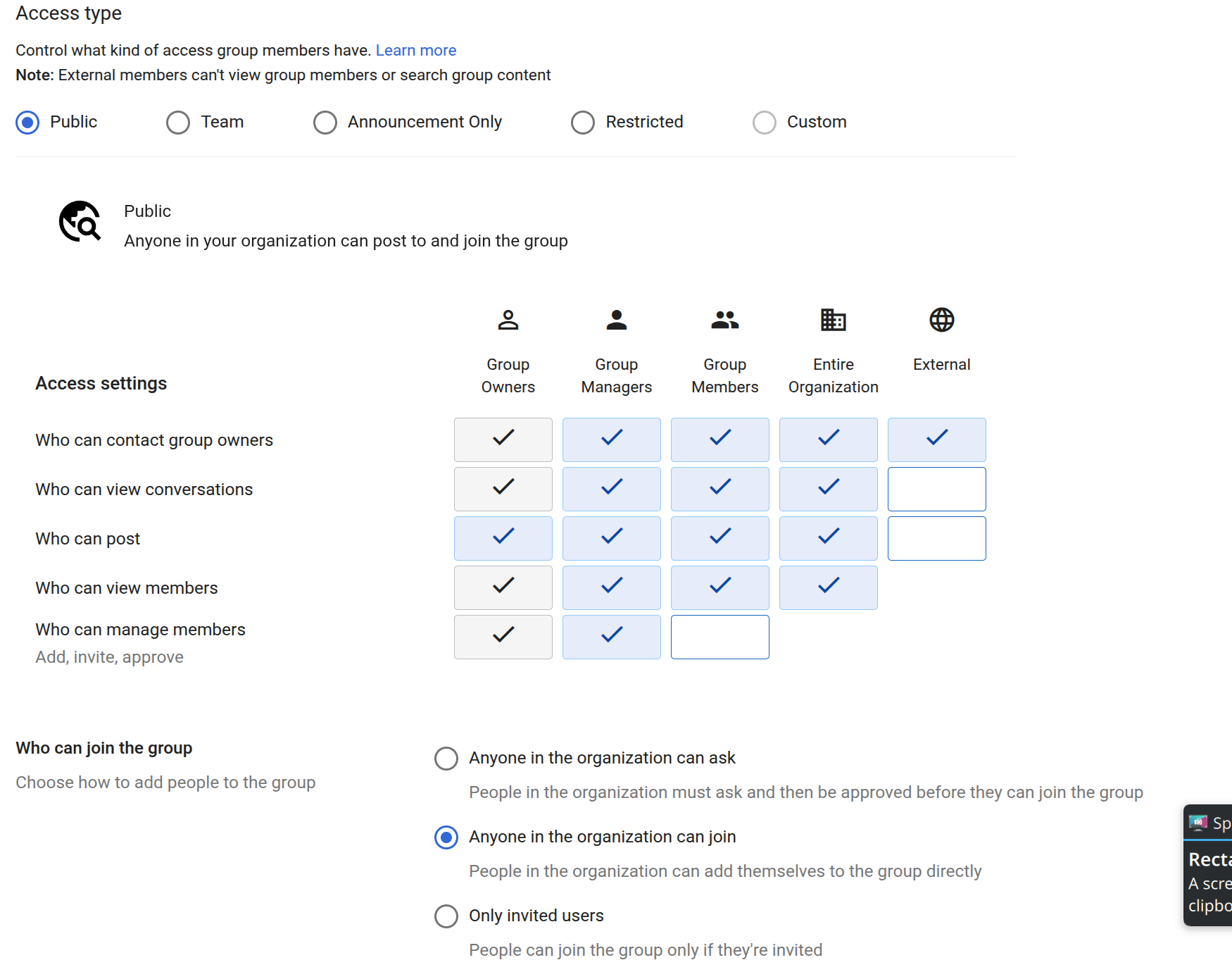
I've had admin powers at 5+ companies' Google Workspace/G Suite over the past decade or so. Every single one had groups which were misconfigured, often so anyone in the whole company could join without approval or see the message history at https://groups.google.com without being a member at all.
This is because for any sensible configuration of Google Groups when using it for email groups you have to use the "Custom" permissions mode. The default Public mode doesn't allow external people to email the group, but does allow the whole company to see all the messages. The default Team mode, has the same problem of everyone being able to see all the messages.
Also let's not forget that dangerous little "Anyone in the organisation can join" toggle at the bottom which is on by default. So any random new starter can join your confidential company directors group and get all the emails sent to it.
Giving Google the benefit of the doubt here, I think the reasoning might be that Google Groups is intended as a kind of company forum, not for private email groups. However that isn't how anyone uses it in my experience...


![[?]](https://objects.transitory.social/sharkey-media/8a2e1184-dfb5-4632-b6d1-ca5d0fd76a15.png)