Search results for tag #networking
Upcoming "Network Management with the OpenBSD Packet Filter Toolset" tutorials (covering #freebsd and #openbsd):
2026-03-19 AsiaBSDCob https://www.asiabsdcon.org
2026-06-18 BSDCan https://www.bsdcan.org
See https://nxdomain.no/~peter/pf_tutorial_upcoming_questions_welcome.html (https://bsdly.blogspot.com/2025/05/for-upcoming-pf-tutorials-we-welcome.html)
and https://nxdomain.no/~peter/what_is_bsd_come_to_a_conference_to_find_out.html (https://bsdly.blogspot.com/2025/11/what-is-bsd-come-to-conference-to-find.html)
plus https://nxdomain.no/~peter/yes_the_book_of_pf_4th_ed_is_coming.html (https://bsdly.blogspot.com/2025/07/yes-book-of-pf-4th-edition-is-coming.html)
Registration for BSDCan 2026 is open at https://www.bsdcan.org/2026/registration.html + tutorial schedule published.
#bsdcan #freebsd #openbsd #netbsd #development #networking #devops #sysadmin #conferences
For more on BSD and the BSD conferences, see https://nxdomain.no/~peter/what_is_bsd_come_to_a_conference_to_find_out.html (or tracked https://bsdly.blogspot.com/2025/11/what-is-bsd-come-to-conference-to-find.html +
https://medium.com/@peter.hansteen/what-is-bsd-come-to-a-conference-to-find-out-06acd7d77fd8 )
New blog post: Running your own Autonomous System on FreeBSD.
Got an AS number and IPv6 /48 via RIPE, set up a FreeBSD BGP router with FRR, two upstreams, and built GRE/GIF tunnels ti bring my own globally routable addresses to servers at different providers.
The interesting part: dual-FIB policy routing lets FreeBSD jails speak from both provider and BGP addresses simultaneously.
https://blog.hofstede.it/running-your-own-as-bgp-on-freebsd-with-frr-gre-tunnels-and-policy-routing/
Registration for BSDCan 2026 is now open https://www.bsdcan.org/2026/registration.html and tutorials schedule is published.
#bsdcan #openbsd #netbsd #freebsd #libresoftware #freesoftware #conference #development #networking #sysadmin #devops
My website "hofstede.it" now lives in my own AS201379 on my asigned IP-addresses 🙂
https://bgp.tools/prefix/2a06:9801:1c::/48#asinfo
Running my own BGP router in LONAP (London) with FreeBSD and FRR, where I announce my network 2a06:9801:1c::/48 to the internet.
Peering is still fairly limited, but that'll improve within the next weeks, when I get 2 additional peers 🙂
#networking #ipv6 #peering #bgp #selfhosting #engineering #devops #freebsd
* Previously in the week it was noticed that Cilium had an update to 1.19.0 Incident report:
Incident report: 
* Upon further inspection, this looked to be a pre-release, so it was left alone, cilium is a load-bearing component and should only be touched with care
* At some point in the last week I forgot about that and hit merge in forgejo, not an issue, since argocd won't auto-sync any load-bearing components (cilium, forgejo, argo, cert-manger, and a handful of others)
* Over the last few days I have repeatedly restarted various components while troubleshooting some OIDC issues. Including ArgoCD and Forgejo
* This caused a few sync errors or argo state refresh errors as pods were unceremoniously exploded
* At some point during this time Cilium ended up out of sync/errored
* By this point I had forgotten about the cilium major* update
* I hit sync to clear that out and see what is wrong. Everything is green, and nothing breaks.
* BGP sessions continue
* I go about my afternoon
* BGP sessions expire, causing immediate issues. since my old config was depricated
* I start the investigation with DNS, since the TV stopped playback and sites stopped loading on my laptop
* Yup, DNS is down.
* But not from my dev console, that means ad-guard DNS is down.
* Ad-guard DNS is throwing errors connecting to quad9 via DoT, I am not sure the cause of this, maybe the UI has a clue
* ad-guard DNS ui isn't opening, oh. No cluster-based site is opening actually.
* Confirmed, all LB services are down, must be BGP related
* Looking in the Mikrotik router I see two BGP sessions, so I restart the BGP service on the router, they drop and don't re-appear, must have been stale on that side.
* Restart cilium to see logs
* BGP config error? Wait, did cilium update???
⚠️ You may need to take action during upgrade to Cilium v1.19 if you use Network Policies, Cluster Mesh, LoadBalancer IPAM or BGP.* Oh right, I've been seeing depreciation warnings about the BGP config for ages now
* After converting the docs format I am rewarded with the TV abruptly starting the playlist, time to commit this to git and move on, phew

#Homelab #Networking #Kubernetes #BGP
LibreSpeed is a lightweight, open-source internet speed test you can fully self-host.
No trackers, no Flash/Java, no forced telemetry just download, upload, ping, and jitter. A privacy-friendly alternative to Speedtest.net and Fast.com.
👉 https://github.com/librespeed/speedtest
👉 More tools like this: https://digital-escape-tools-phi.vercel.app/
#Privacy #OpenSource #SelfHosting #Networking #FOSS #DeGoogle
A blog series on my descent into maddness with PKI/etc would probably be interesting But first I can finish out the networking series ( The last part for now will be about taking the engress policy features and wireguard and then creating a wireguard interface on a Talos linux node, and then assigning routing rules to a non-default table, so only traffic assigned to that interface uses it. The end result: ability to create a egress policy targeting a pod, and send all outbound traffic out over that VPN link. I could have done this for the web services that I am having exit on the cloud node, but I want to eventually put caching on the edge. Of course the goal here with the wireguard exit was to use ProtonVPN for a download client......
The Rest Is Trash https://nxdomain.no/~peter/the_rest_is_trash.html (tracked https://bsdly.blogspot.com/2026/02/the-rest-is-trash.html) following up on #greytrapping, updating the 18 years piece https://nxdomain.no/~peter/eighteen_years_of_greytrapping.html #openbsd #spamd #greytrappng #greylisting #antispam #cybercrime #networking # spam
Tonight the waves of bot traffic hitting many of the servers I manage have intensified, including Brew on BSD Cafe, but not only that. Honestly, the feeling I have now is no longer the same as it was some time ago (AI scrapers), but that there are real disruption operations going on. I can see it’s much more concentrated around certain providers and certain datacenters. If I block some countries like China, the numbers drop dramatically.
I still haven’t figured out whether there’s something specific and targeted happening (a broad DDoS) or if they’re still scrapers, but they honestly seem really dumb.
Maybe we should just create an alternative network and leave the Internet to these entities.
At this point they’re just talking to themselves anyway.
Assume two machines in the same network each have a link-local address (LLA) and a unique-local address (ULA). They could talk to each other with either address. Is there some kind of prioritizing the one over the other, e.g. always use LLA if available else use ULA?
The first scheduled "Network Management with the OpenBSD PF Toolset" session of the year will be at AsiaBSDCon 2026 https://2026.asiabsdcon.org/index.html.en, https://2026.asiabsdcon.org/entry/talk/ZUQPMV/, registration to open soon.
Also see https://nxdomain.no/~peter/what_is_bsd_come_to_a_conference_to_find_out.html #asiabsdcon #freebsd #openbsd #pf #packetfilter #networking #conference @nostarch @stucchimax
Oh, I suppose I have been slacking and not telling you that if you order The Book of PF, 4th ed https://nostarch.com/book-of-pf-4th-edition now, you will get the *final version* ebook (print is still in progress) #bookofpf #openbsd #freebsd #networking #firewalls #pf #networktrickery #freesoftware #libresoftware @nostarch
Also see https://nxdomain.no/~peter/yes_the_book_of_pf_4th_ed_is_coming.html
Nice article about the nuances of IPv6 local addressing
https://blog.apnic.net/2020/05/20/getting-ipv6-private-addressing-right/
Need to expose a service running inside a Bastille jail? Use the `bastille rdr` command to easily map a port from the host to the jailed system.
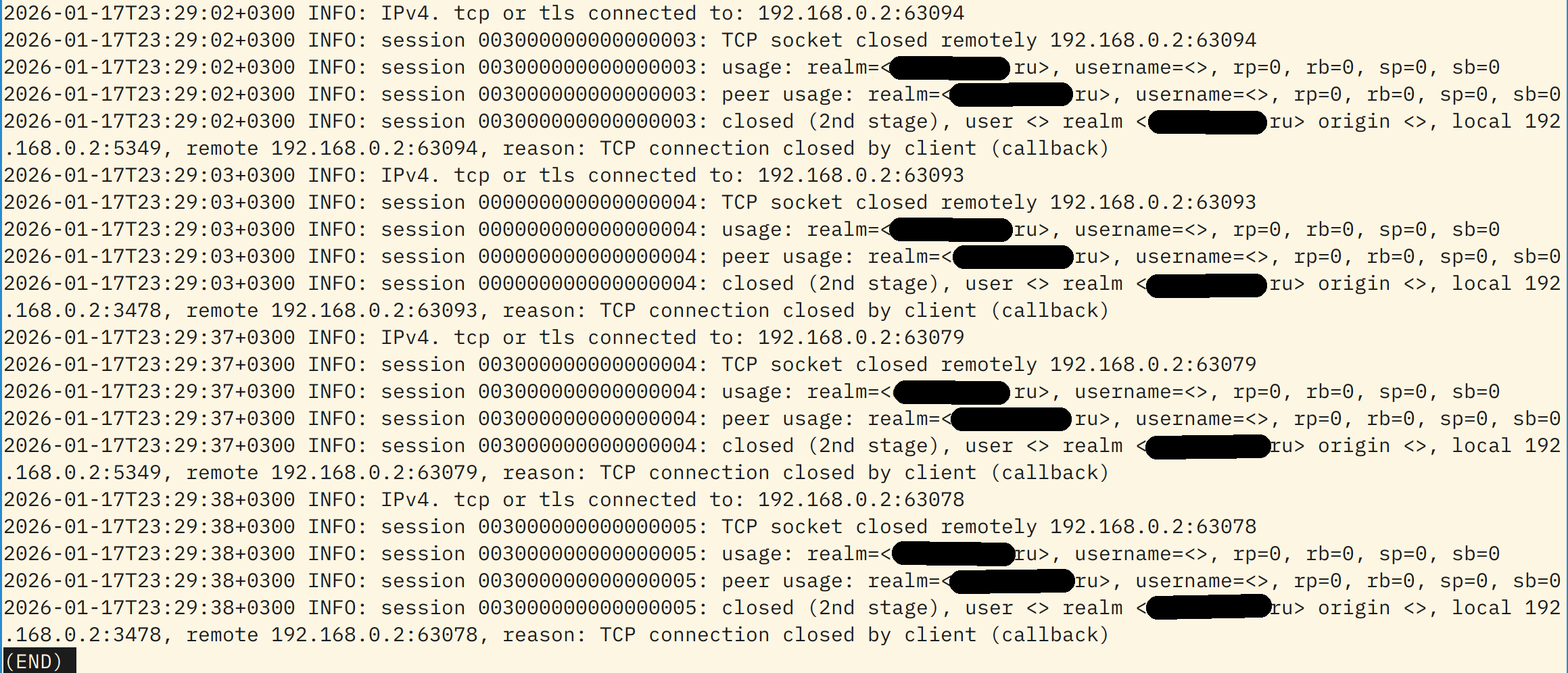
Few days ago I successfully configured #coturn to have a TURN/STUN server for in-family calls. But … looks like bots or some bad guys constantly trying to connect to my TURN server to use it for something :-(
Of course, it is impossible, since anonymous access or any other access without right key is impossible. But, there are no IPs of attackers in the log file, even wth "Verbose" directive — only my local and public IPs and my server's hostname 
Maybe, there is some way to force coturn to display IP addresses of connected clients, so I could ban them all with fail2ban?
I am in @EUCommission’s Berlaymont building, connected to the EC_Guest WiFi.
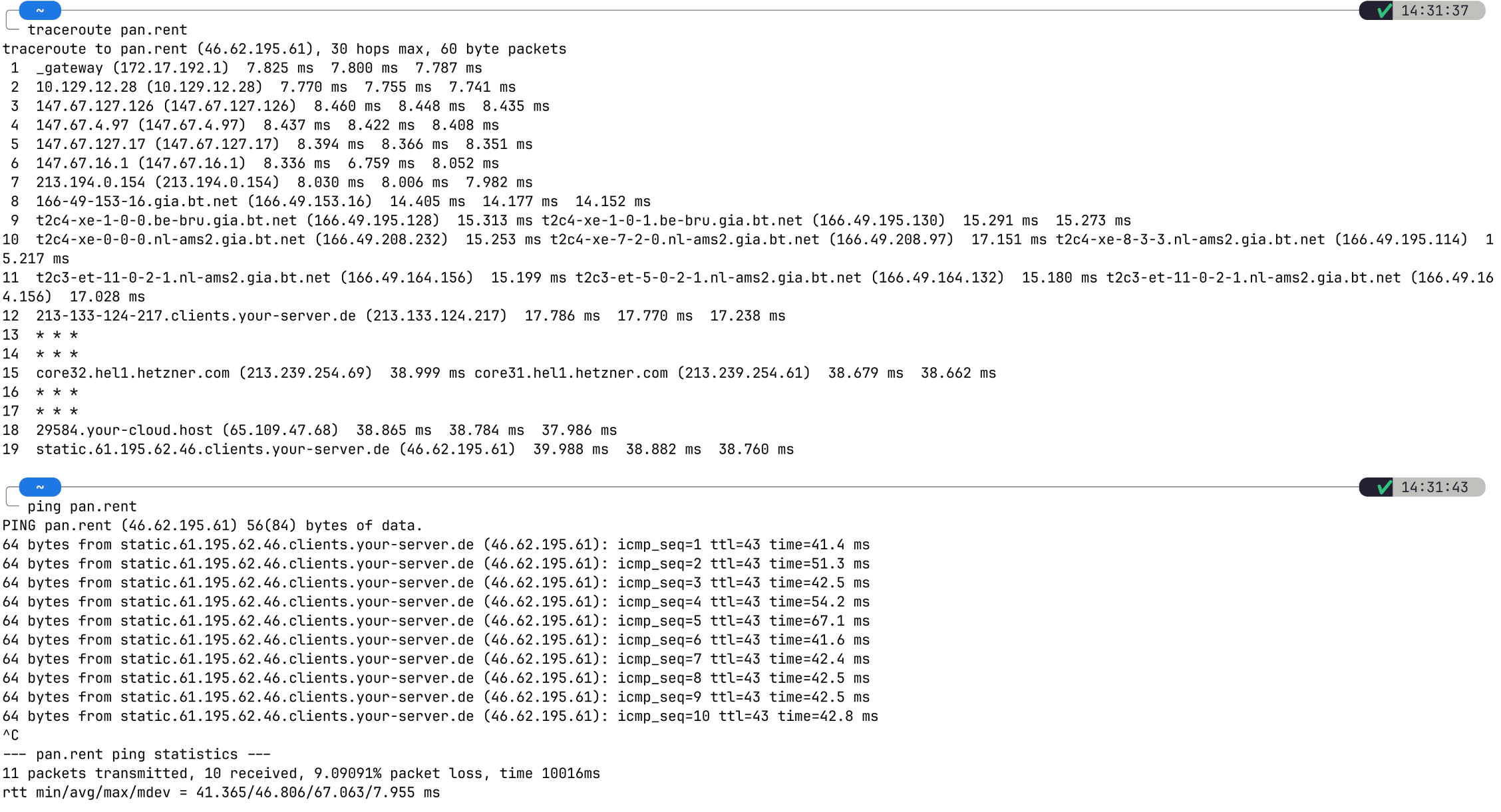
Very weird and interesting: pan.rent is blocked by the firewall. I can ping and traceroute our server, but I cannot load it via Web interface nor via API. It works with a VPN, though.
I need a long distance (~300m) network connection through forest. Wireless or lasers don't like any obstacles so I need to rule them out.
Cat6 official max distance is 100m, but what if I would slow the speed down to 10mbps - would it allow longer cable runs? Online searches reveal that there is lot of ai-generated or just copied content without answers.
3 more days!
BSDCan 2026 is now accepting submissions for the June 2026 conference, see https://www.bsdcan.org/2026/papers.html and links therein for instructions.
Submissions deadline is January 17, 2026, the conference runs tutorials June 17-18, talks June 19-20.
#bsdcan #conference #freebsd #netbsd #openbsd #bsd #development #networking #freesoftware #libresoftware
rpki-client 9.7 released https://undeadly.org/cgi?action=article;sid=20260114104154 #openbsd #rpkiclient #rpki #routing #security #networking #bgp
I wish there was a switch/option on the ip (-6) route show command to sort correctly by prefix and preflix length. #linux #networking
LACP mode removed from trunk(4) https://www.undeadly.org/cgi?action=article;sid=20260113070814 #openbsd #networking #trunk #lacp #development #current
A Major Mail Provider Demonstrate They Likely Do Not Understand Mail At All https://nxdomain.no/~peter/they_do_not_understand_mail_at_all.html (tracked https://bsdly.blogspot.com/2026/01/a-major-mail-provider-demonstrate-they.html)
#greytrapping #spam, #antispam #greylisting #blocklist, #openbsd #freebsd #smtp #email #SMTP, #contentfiltering #SPF #DMARC #security #networking
Never miss a chance to criticize, and don’t lose sleep over rejecting a job at a company whose electrical installation is a total shitshow ✌️
#NetMCR (https://www.netmcr.uk/) in #Manchester is on tomorrow (8th January) at the Northern Monk (https://www.northernmonk.com/pages/manchester) from 7pm.
Tim Panton will be talking about ‘Quantifying 5G Uplink Performance From a Moving Vehicle’
Sounds complicated/interesting 😀
Go and chat with some nice people, have some weird 🍻, and if you're hungry, 🍔 and 🍟!
When adopting a new 100GbE switch, it’s important to follow gradual introduction procedures to keep your existing cats from becoming stressed and developing RDMA aggression.
And as always, we value your input, see "For Upcoming PF Tutorials, We Welcome Your Questions" https://nxdomain.no/~peter/pf_tutorial_upcoming_questions_welcome.html (tracked https://bsdly.blogspot.com/2025/05/for-upcoming-pf-tutorials-we-welcome.html) #pf #firewall #tutorial #openbsd #freebsd #networking #security #ipv6 #ipv4 @stucchimax
There will be a "Network Management with the OpenBSD Packet Filter Toolset" at AsiaBSDCon in Taipei Thursday, March 19 2026.
Yours truly and Max Stucchi teaching networking goodness.
Details soon to emerge at https://2026.asiabsdcon.org/ #asiabsdcon #freebsd #openbsd #networking #conference #tutorial #pf #packetfilter #security #firewall #freesofware #libresoftware @stucchimax
Maybe #AskFedi will surprise me... my all-in-one crap ass ISP modem/router/wifi/whatever only has 4 gigabit LAN ports.
I'd like to bridge-mode it and get a replacement with 6+ gigabit LAN ports, any suggestions shipping within the EU?
Boosts welcome. #networking #hardware
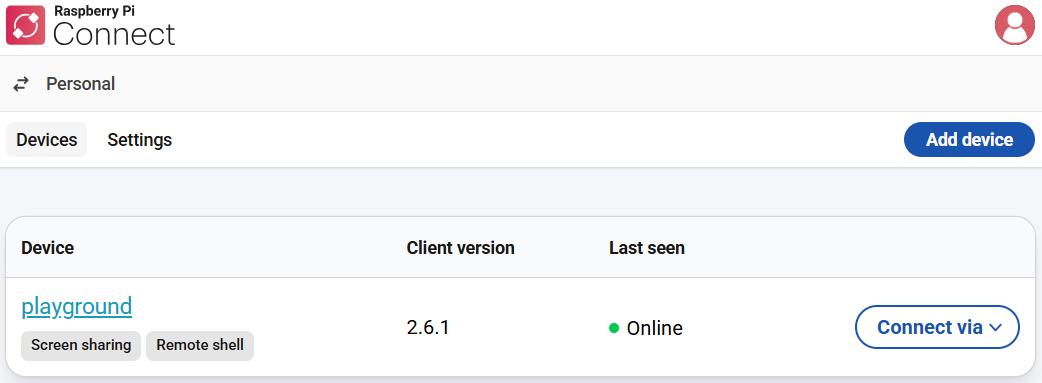
Playground setup with Raspberry Pi 5 and Mikrotik hEX router.
The Pi, with a M.2 HAT+ Compact, is running Raspberry Pi OS Desktop.
The hEX is running RouterOS 7.20.6, without a default configuration. Right now it's acting more like a switch.
I'm using Raspberry Pi Connect to access the Pi from outside my home network, and mostly ssh and WinBox to access the devices when inside, but Connect also works here.
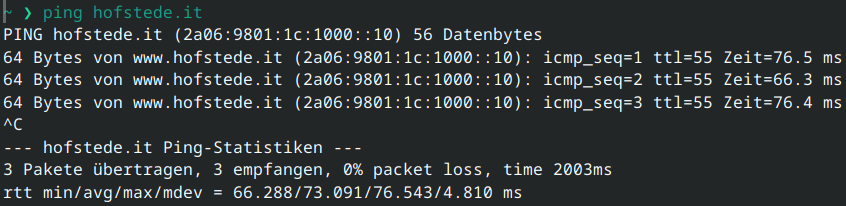
I’ve been losing my mind for almost 4 hours, and I feel like an idiot.
At first I couldn't understand why the TLS handshake was always taking more than 300 milliseconds. I thought it was a local or server-side issue. Only after about an hour did I test google.com and saw the exact same behavior.
That's when I realized that with my other WAN connection, the timing drops significantly.
So I started going crazy over my MikroTik configuration, convinced it had to be something related to multi-WAN. I even briefly asked an AI (I know, I know...), which said the problem was probably my neighbor, who had eaten too much pizza.
At that point, I kept spiraling.
Then it hit me that the Vodafone Station has its built-in Wi-Fi disabled, since I manage the network behind it. I could enable it and bypass the MikroTik. I enabled it and ran a direct test.
Bingo. Same problem.
So the issue is upstream. I suspect it’s "Vodafone Rete Sicura", some awful thing I never wanted and that probably does some kind of traffic inspection.
I really can't wait for FTTH to arrive so I can finally get rid of this stuff.
Friends, at the end of a horrible year, please let's talk about something *nice*.
My EUR 0.02: You Have Installed OpenBSD. Now For The Daily Tasks. https://nxdomain.no/~peter/openbsd_installed_now_for_the_daily_tasks.html (tracked https://bsdly.blogspot.com/2024/09/you-have-installed-openbsd-now-for.html)
Bonus track: Yes, The Book of PF, 4th Edition Is Coming Soon https://nxdomain.no/~peter/yes_the_book_of_pf_4th_ed_is_coming.html (tracked https://bsdly.blogspot.com/2025/07/yes-book-of-pf-4th-edition-is-coming.html)
#freesoftware #openbsd #freebsd #bookofpf #networking #security #deveops #development #sysadmin @nostarch


![[?]](https://objects.transitory.social/sharkey-media/8a2e1184-dfb5-4632-b6d1-ca5d0fd76a15.png)



 [
[