Search results for tag #ipv6
NAT64 things:
I'm currently just using Tayga on opnsense, but its actual operation is quite opaque. It's simple enough to just turn on, but I'm having little bits of "network gremlins" at times that I've not hunted down but smell like pool exhaustion or other issues with longer running connections.
What's the word on Jool these days? This will end up being More To Run ™️ , but dropping Jool instances on a couple of mini PCs could give some extra visibility with e.g. https://github.com/cooperlees/jool-exporter or even just jool stats. Worth it?
Tayga advertises as a stateless NAT64, which, like "fair" as it does 1:1 6to4 translation without any explicitly connection tracking, but it still does do dynamic mapping assignment from your v4 pool. That's still a NAT table which is state tracking in my book, but I guess it's "quasi stateless" since it's not doing full conntrack type behaviour?
Anyway: For a home setup, just doing regular stateful NAT64 seems sensible enough if going the jool route, yea?
It looks like I solved the #Thunderbird #IPv6 #problem by setting
mailnews.tcptimeout 100-> 250
in Thunderbird #config . Unsure this is permanent fix, but till now the problems are gone. Unsure what Thunderbird does, because network is fast here and the sogo/dovecot/postfix mail server is locally here.
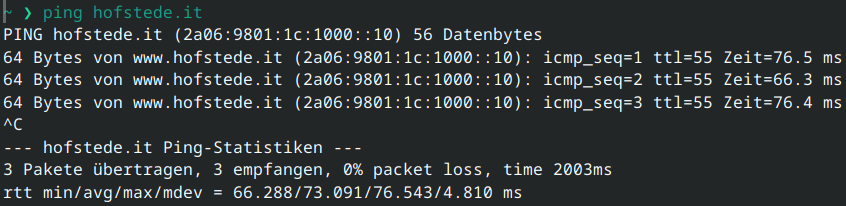
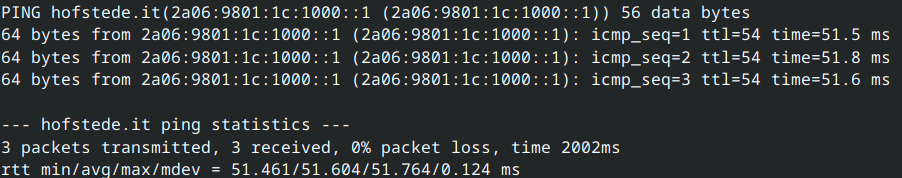
New blog post: PF Firewall on FreeBSD - A Practical Guide
After years of running PF across multiple FreeBSD servers, I've written up the patterns that work: macros, tables, brute-force protection, NAT for jails, and dual-stack filtering.
Covers everything from basic concepts to production configs, plus a sidebar on authpf for bastion hosts.
If you're running FreeBSD and want a firewall that's elegant, powerful, and actually understandable, PF is worth your time.
https://blog.hofstede.it/pf-firewall-on-freebsd-a-practical-guide/
#FreeBSD #PF #Firewall #Security #Jails #SysAdmin #IPv6
New blog post: Running your own Autonomous System on FreeBSD.
Got an AS number and IPv6 /48 via RIPE, set up a FreeBSD BGP router with FRR, two upstreams, and built GRE/GIF tunnels ti bring my own globally routable addresses to servers at different providers.
The interesting part: dual-FIB policy routing lets FreeBSD jails speak from both provider and BGP addresses simultaneously.
https://blog.hofstede.it/running-your-own-as-bgp-on-freebsd-with-frr-gre-tunnels-and-policy-routing/
My website "hofstede.it" now lives in my own AS201379 on my asigned IP-addresses 🙂
https://bgp.tools/prefix/2a06:9801:1c::/48#asinfo
Running my own BGP router in LONAP (London) with FreeBSD and FRR, where I announce my network 2a06:9801:1c::/48 to the internet.
Peering is still fairly limited, but that'll improve within the next weeks, when I get 2 additional peers 🙂
#networking #ipv6 #peering #bgp #selfhosting #engineering #devops #freebsd
Bandcamp uses Fastly, so it would be relatively easy for them to enable #IPv6 : https://www.fastly.com/documentation/guides/full-site-delivery/domains-and-origins/enabling-dualstack-connections/
I keep coming across programs that still prefer IPv4 even when a viable #IPv6 path is available. Part of me wants to file bug reports to get them to follow the spec. The other part of me just finds a way to return an IPv6-only record for the thing I want to talk to and it usually works.
RE: https://fosstodon.org/@iscdotorg/116008189795385090
And I'm sure Android still won't support it
#ipv6
Aos usuários #BR de #Ubuntu e Internet da dona roxa (Vivo - AS18881): neste momento tem 02 (dois) servidores espelho (mirrors) de pacotes com latência nacional em #IPv6 :
- https://linorg.usp.br/ubuntu
- https://mirrors.ic.unicamp.br/ubuntu
Essa empresa tem o péssimo hábito de fazer conexões locais irem passear na terra do camundongo e, por algum motivo, desde a manhã de hoje e somente pra esses mirrors tá funcionando como deveria. Aproveitem enquanto não "desconsertam".
Explico em: https://ipv6.reddit.com/r/InternetBrasil/comments/1qtyihx/problemas_na_vivo_de_repente_destinos_nacionals
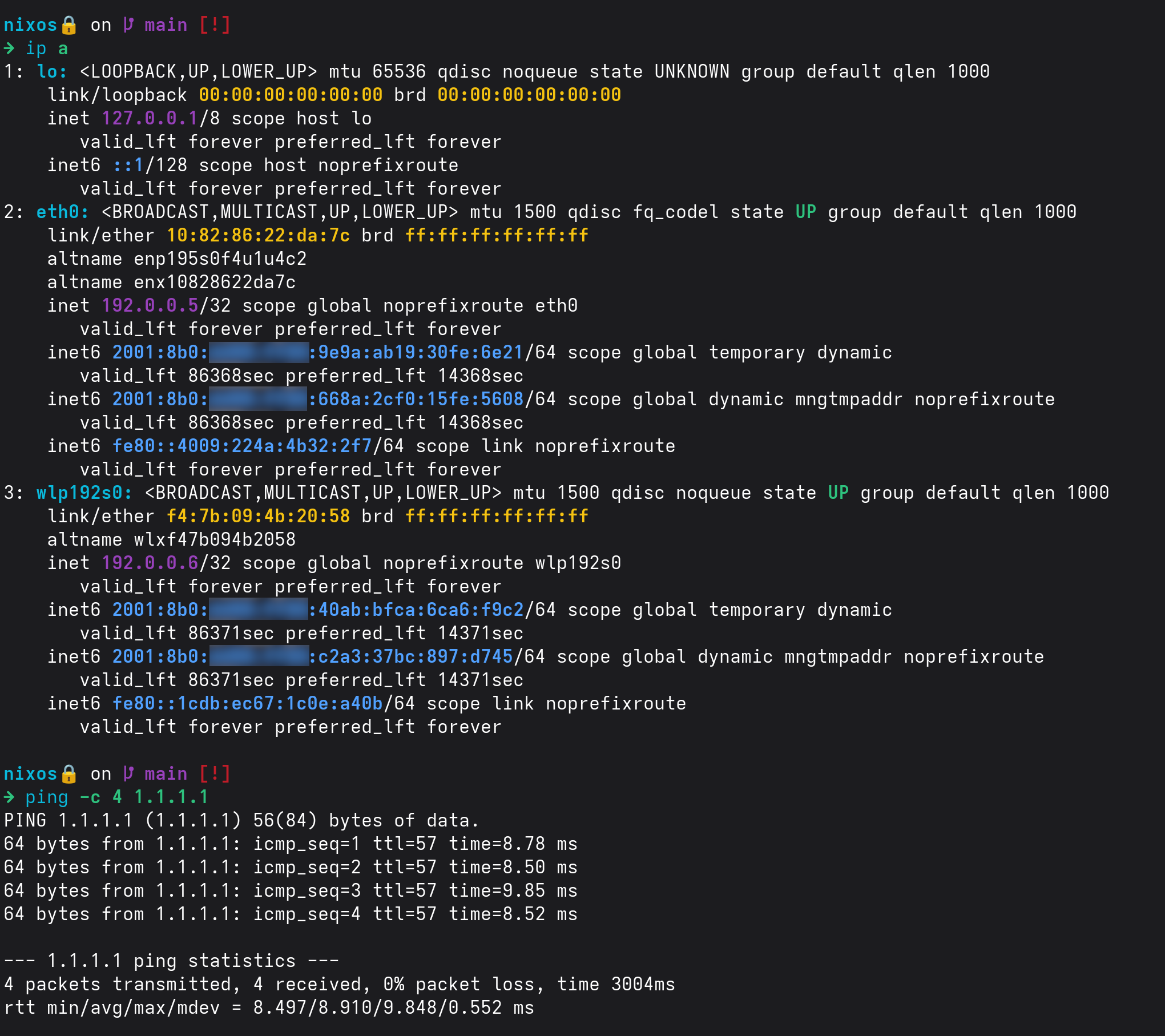
NetworkManager based CLAT working on NixOS! 
This took me way too long to get this working, but it works really well!
Here's an awful gist if anyone wants to try:
https://gist.github.com/alexhaydock/3a458b36ce79851f4576794e5f18e1d5
Feel free to tell me all the ways I did the Nix wrong
(seriously though, I'm quite new to Nix. pls send help  )
)
It's 2026 and idiotic company sunrise mobile still doesn't know how to do IPv6 on APN's.
Enjoy CGNAT!
#Switzerland #mobile #networks #sunrisemobile #sunrise #ipv6 #ipv4
@fosdem as is tradition: the photo from the closing talk of #FOSDEM
Of note:
* Next year, the default network of #FOSDEM will be #IPv6 only. At lot of things will break, and this is intentional
* FOSDEM will become political. If you are in policy, politics, a position of power: reach out to us at policy@fosdem.org
Love that FOSDEM and the rest of the OSS community is catching up to where I was 12 years ago: https://blog.flyingpenguintech.org/2013/11/cookienet.html
Amazon RDS now supports IPv6 for VPC endpoints of RDS Service APIs
Posted on: Jan 30, 2026
https://aws.amazon.com/about-aws/whats-new/2026/01/amazon-rds-ipv6-vpc-endpoints-service-apis/
i have inet6 autoconf in my /etc/hostname.iwm0 and from time to time i get this in my logs (endless repetition):
Jan 29 07:48:56 s0 /bsd: iwm0: DAD detected duplicate IPv6 address [redacted] NS in/out=1/1, NA in=0
Jan 29 07:48:56 s0 /bsd: iwm0: DAD complete for [redacted] - duplicate found
Jan 29 07:48:56 s0 /bsd: iwm0: manual intervention required
when this happens ipv6 stops working. a restart of my laptop most of the times solves this. is this something for the mailing list? something to do with my local network?
Assume two machines in the same network each have a link-local address (LLA) and a unique-local address (ULA). They could talk to each other with either address. Is there some kind of prioritizing the one over the other, e.g. always use LLA if available else use ULA?
Every so often I randomly recall that my colleague...
deployed our ENTIRE new AWS networking setup
with IPv6 DISABLED
for no good reason.
RE: https://mastodon.social/@sundogplanets/115968263886391318
This is basically me and #ipv6.
Anyway, fairly petty things to complain about, given everything else that's happening.
But pollution from satellite internet is my thing that I'm an expert on! So I will keep complaining about it and educating people about it. This is the fight that all my training has prepared me for, so I'm fighting it!
IAM Identity Center now supports IPv6
by Suchintya Dandapat on 26 JAN 2026
https://aws.amazon.com/blogs/security/iam-identity-center-now-supports-ipv6/
Whoa! I actually got one fixed. Reasonably quick to boot!
https://github.com/glowing-bear/glowing-bear/issues/1300
Sadly the project seems to be dormant. Good news is I was able to deploy the static tarball on my own website so I can have all #IPv6 for myself.
If you are a Netlify customer, can you please file a ticket requesting this be changed?
> By default, IPv6 is not enabled on all Netlify sites and apps. If you use Netlify DNS, you can enable it explicitly in your Domains dashboard.
ref: https://docs.netlify.com/manage/domains/configure-domains/enable-ipv6/
I guess a little more info is warranted. This is https://github.com/traefik/whoami running on an LXC in my homelab with a for-reals IPv6 address from my leased /48 routed from a VPS running in Vultr to my Mikrotik via a Wireguard tunnel. No proxies, no port forwarding, no shenanigans. I have verbose logging turned on just to get counts and I'll probably wipe it tomorrow.
If anyone would be willing to click this link and tell me if it worked for you, I'd be ever so grateful.
This is one of those things that should have been obvious, but I just schlepped along with it until it finally got annoying enough to fix.
Docker networking things!
Docker does have some docs for IPv6 networking for a bit now that's been not quite as terrible as it used to be. To be clear: It's still standard docker things so "NAT ALL TEH THINGS," but at least you'll get IPv6 connectivity.
So I'd followed https://docs.docker.com/engine/daemon/ipv6/ to:
- enable IPv6 as a whole
- add an IPv6 supernet from which new networks will get allocated (IPAM)
- add IPv6 for the default docker bridge
Basically:
{
"ipv6": true,
"fixed-cidr-v6": "<your ULA base>::/64",
"default-address-pools": [
{ "base": "172.17.0.0/16", "size": 24 },
{ "base": "<your ULA>::/56", "size": 64 }
]
}
However, if you're using compose for things, you still will not get IPv6 by default and will need to create an explicit IPv6-enabled network in your compose specification and then add that network to all of your containers.
The missing bit was actually changing the default settings of the bridge network driver in the Docker daemon config. This took a bit of hunting around, but the option is com.docker.network.enable_ipv6. So, add:
"default-network-opts": {
"bridge": {
"com.docker.network.enable_ipv6": "true"
}
}
For a full config like:
{
"ipv6": true,
"fixed-cidr-v6": "<your ULA base>::/64",
"default-address-pools": [
{ "base": "172.17.0.0/16", "size": 24 },
{ "base": "<your ULA>::/56", "size": 64 }
],
"default-network-opts": {
"bridge": {
"com.docker.network.enable_ipv6": "true"
}
}
}Huzzah! Any new docker networks, specifically including any networks from compose files, will now get IPv6 by default!
#IPv6 project updates:
- I leased a /48 from https://freerangecloud.com and figured out how to get Bird to announce it from a Vultr VPS (shockingly cheap, $5/mo VPS + $8/year for the prefix)
- Took multiple hours last night and this morning but I finally got a /56 of that delegated into my #homelab over a Wireguard tunnel, including proper routing and return paths.
- I also have my Comcast-provided /60 delegated out to a couple VLANs and am shoving it into Mikrotik static DNS records.
My vague concept of a plan is now to get NAT64 and DNS64 working on another Vultr-delegated IPv6-only VLAN and then stick a VM there with some public services. Once I have that working I can think about bringing VMSave back onto #selfhosted infra and retiring that VPS.
Routing the #IPv6 /56 took a long time to figure out because I think the tutorials and forum posts I was trying to work from were out of date wrt what Mikrotik can do these days with simple routing rules. Once I abandoned the weird mangle rules those posts were telling me to use and went with what this blog post describes everything started working great:
I was trying to use Claude to help and ultimately that was completely useless. I guess not completely, it reinforced that I definitely can't rely on anything it says without citations.
Ich habe das mal hier festgehalten.
https://www.thomas--schaefer.de/wireguard-mit-GUA-und-ULA.html
Ich hoffe die Detailtiefe ist ausreichend.
Die Schlüssel wurden für den Text neu generiert - also nicht erst versuchen(und auch nicht übernehmen 😉, das selbe gilt für die IP-Adressen, ich habe nicht den Dokumentationsadressraum verwendet.)
Ooh  BPF-based CLAT has been merged into NetworkManager
BPF-based CLAT has been merged into NetworkManager
https://gitlab.freedesktop.org/NetworkManager/NetworkManager/-/merge_requests/2107
Can be tested on Fedora with the `networkmanager/NetworkManager-main` COPR repo
#NetworkManager will now include #CLAT capabilities: https://gitlab.freedesktop.org/NetworkManager/NetworkManager/-/merge_requests/2107 is now merged, functionality will be available on the next release.
Thanks to everyone involved 🙂


![Hmm. We're having trouble finding that site.
We can't connect to the server at rdumesh.org.
If you entered the right address, you can:
* Try again later
* Check your network connection
* Check that Firefox has permssion to access the web (you might be connected but behind a firewall)
[Try Again] Hmm. We're having trouble finding that site.
We can't connect to the server at rdumesh.org.
If you entered the right address, you can:
* Try again later
* Check your network connection
* Check that Firefox has permssion to access the web (you might be connected but behind a firewall)
[Try Again]](https://cdn.tenforward.social/media_attachments/files/116/024/820/393/247/237/original/80cbd9285ad15e5f.png)





![AIllowed IP ranges (optional)
Must be valid CIDR notation.
Input Range 1: [text input] 185.15.56.0/25
Input Range 2: [text input] 2a02:ec80:a000::/56 [warning icon, red background]
One or more fields contains an invalid CIDR entry. AIllowed IP ranges (optional)
Must be valid CIDR notation.
Input Range 1: [text input] 185.15.56.0/25
Input Range 2: [text input] 2a02:ec80:a000::/56 [warning icon, red background]
One or more fields contains an invalid CIDR entry.](https://cdn.masto.host/wikisworld/media_attachments/files/115/984/129/136/166/344/original/e353fc09d3ce5c4f.png)

