Search results for tag #networking
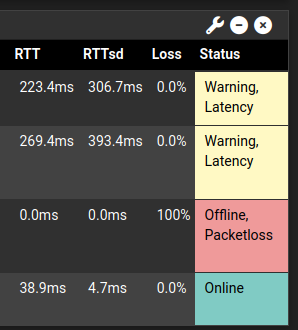
Either @quad9dns 's 9.9.9.9 & 9.9.9.11 are down or my #ISP (#Vodafone #Germany) is fucking around with my traffic to hide their #downtime...
- Given that their own shitty speedtest doesn't load and @Speedtest /
speedtest-cliis unable to connect to any testing servers, I'd assume they fuck with my #traffic.
I hope @BNetzA, @netblocks, @ooni et. al. take notes, cuz my patience runs thin...
In case anyone wounders: isup is just a ,bash_aliases entry to shorten ping -a -b -c 1 -D ...
#DownForEveryoneOrJustMe #Interwebs #Interwebz #Internets #Internetz #Internet #EDGEland #TechSupport #TechnikerIstInformiert #Schland #diagnostics #Networking #Connectivity #linux #bash #aliases
@Speedtest @BNetzA @netblocks @ooni interestingly, now it reports back the correct, abeit still horrendous latency back after I complained in public.
not shure if @quad9dns had downtime or someone fucked around with my traffic tho...
#DownForEveryoneOrJustMe #Interwebs #Interwebz #Internets #Internetz #Internet #EDGEland #TechSupport #TechnikerIstInformiert #Schland #diagnostics #Networking #Connectivity #BSD #FreeBSD #pfSense
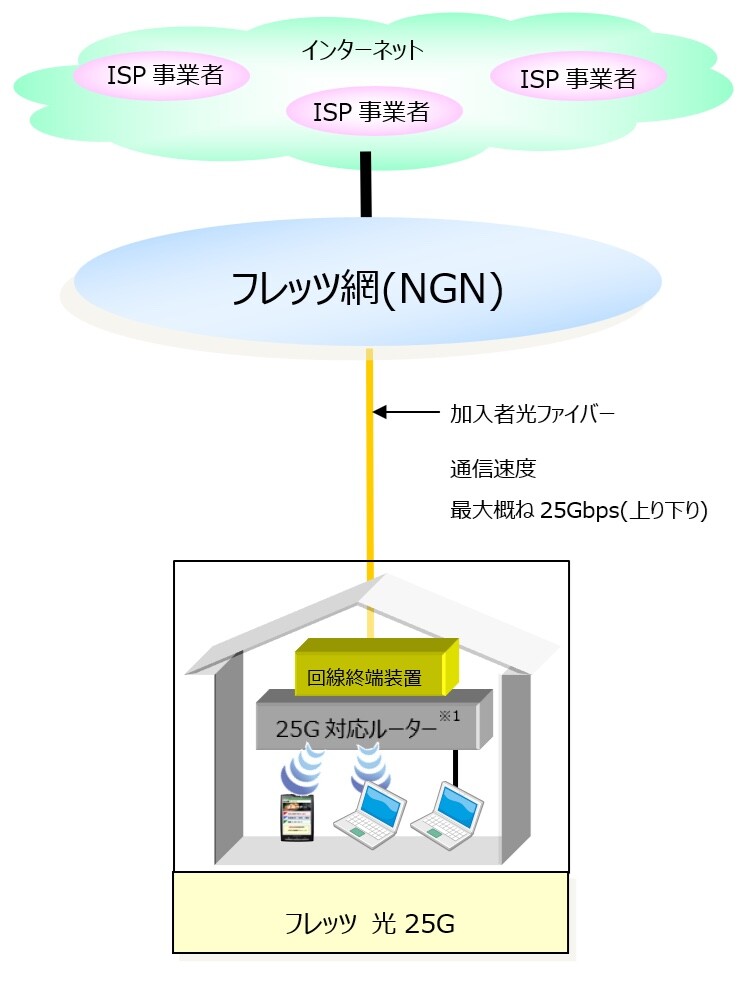
Right after I got 10 gigabit internet at home, NTT Flets (the fiber network I'm on) announces the planned availability of 25 gigabit FTTH next year! They've also started considering offering 50 Gbit to homes…
It took 5 years for 10G to make it from Tokyo down to Kagoshima, so I guess I have another 5 year wait for 25G?
https://www.ntt-east.co.jp/release/detail/20251223_01.html
They also provided this lovely diagram
Anyone know how to change the MAC address properly on OPNsense?
I've tried putting `ifconfig igc1 ether AE:CE:55:0F:F1:CE` in `/etc/start_if.igc1` but it doesn't seem to take.
Yes, I need to actually do the MAC address and not use the proper spoof function since I'm trying to ensure a well-known link-local v6 address (ask me about mDNS at your peril)
Ref: https://forums.freebsd.org/threads/set-mac-address-at-boot.32089/
Wasting bunch of time reducing the public IPv4 usage on AWS for a client to reduce recurring monthly costs (AWS charges by the hour for IPv4s)
There are things AWS doesn’t even support that would help, like giving an RDS instance a public IPv6 without public IPv4. It's dual-stack or die! Please, I don't need any IPv4…
I pray for the day all networking is #IPv6 native and any IPv4 is just gateways for backcompat for laggards…
Being a SysAdmin is hard https://lobste.rs/s/lzmklx #devops #networking
https://about.tree.ht/blog/treehut-outages-december-2025

![Console log Output:
user@x230t:~$ isup 1.1.1.1
PING 1.1.1.1 (1.1.1.1) 56(84) bytes of data.
[1766687889.748671] 64 bytes from 1.1.1.1: icmp_seq=1 ttl=56 time=30.8 ms
--- 1.1.1.1 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 30.804/30.804/30.804/0.000 ms
user@x230t:~$ isup 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
[1766687894.098359] 64 bytes from 8.8.8.8: icmp_seq=1 ttl=116 time=43.8 ms
--- 8.8.8.8 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 43.762/43.762/43.762/0.000 ms
user@x230t:~$ isup 9.9.9.9
PING 9.9.9.9 (9.9.9.9) 56(84) bytes of data.
--- 9.9.9.9 ping statistics ---
1 packets transmitted, 0 received, 100% packet loss, time 0ms
user@x230t:~$ isup 9.9.9.10
PING 9.9.9.10 (9.9.9.10) 56(84) bytes of data.
[1766687914.085668] 64 bytes from 9.9.9.10: icmp_seq=1 ttl=57 time=34.4 ms
--- 9.9.9.10 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 34.366/34.366/34.366/0.000 ms
user@x230t:~$ isup 9.9.9.11
PING 9.9.9.11 (9.9.9.11) 56(84) bytes of data.
--- 9.9.9.11 ping statistics ---
1 packets transmitted, 0 received, 100% packet loss, time 0ms
user@x230t:~$ Console log Output:
user@x230t:~$ isup 1.1.1.1
PING 1.1.1.1 (1.1.1.1) 56(84) bytes of data.
[1766687889.748671] 64 bytes from 1.1.1.1: icmp_seq=1 ttl=56 time=30.8 ms
--- 1.1.1.1 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 30.804/30.804/30.804/0.000 ms
user@x230t:~$ isup 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
[1766687894.098359] 64 bytes from 8.8.8.8: icmp_seq=1 ttl=116 time=43.8 ms
--- 8.8.8.8 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 43.762/43.762/43.762/0.000 ms
user@x230t:~$ isup 9.9.9.9
PING 9.9.9.9 (9.9.9.9) 56(84) bytes of data.
--- 9.9.9.9 ping statistics ---
1 packets transmitted, 0 received, 100% packet loss, time 0ms
user@x230t:~$ isup 9.9.9.10
PING 9.9.9.10 (9.9.9.10) 56(84) bytes of data.
[1766687914.085668] 64 bytes from 9.9.9.10: icmp_seq=1 ttl=57 time=34.4 ms
--- 9.9.9.10 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 34.366/34.366/34.366/0.000 ms
user@x230t:~$ isup 9.9.9.11
PING 9.9.9.11 (9.9.9.11) 56(84) bytes of data.
--- 9.9.9.11 ping statistics ---
1 packets transmitted, 0 received, 100% packet loss, time 0ms
user@x230t:~$](https://media.infosec.space/infosec-space/media_attachments/files/115/781/666/719/666/476/original/5dade4e9ee73f8a3.png)