Search results for tag #security
The lethal trifecta for #AI #agent s: private data, untrusted content, and external communication
https://simonwillison.net/2025/Jun/16/the-lethal-trifecta/
LibreSSL 4.1.1 and 4.0.1 released https://www.undeadly.org/cgi?action=article;sid=20251002054519 #openbsd #libressl #tls #https #cryptography #security #newrelease #development #freesoftware #libresoftware
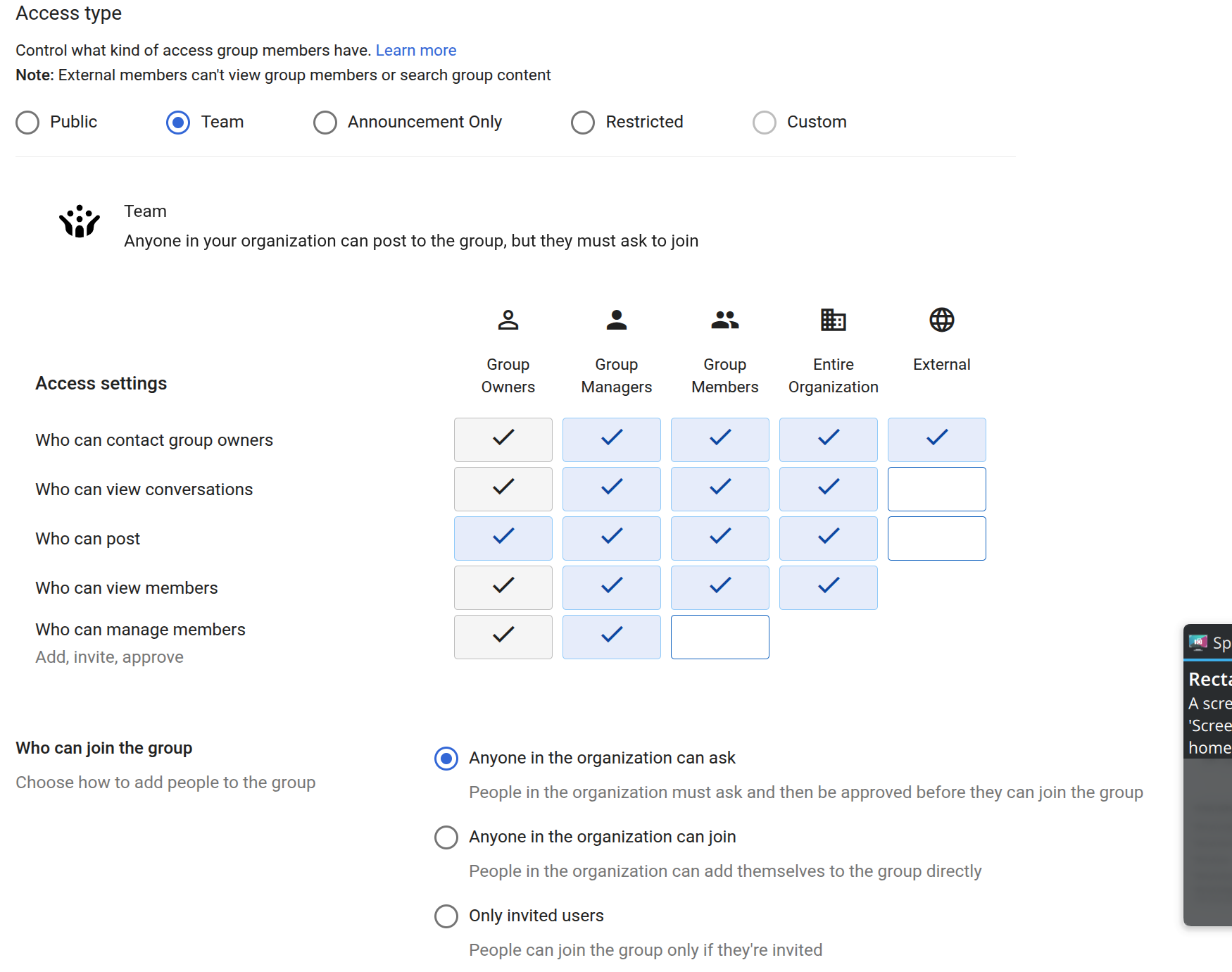
I've had admin powers at 5+ companies' Google Workspace/G Suite over the past decade or so. Every single one had groups which were misconfigured, often so anyone in the whole company could join without approval or see the message history at https://groups.google.com without being a member at all.
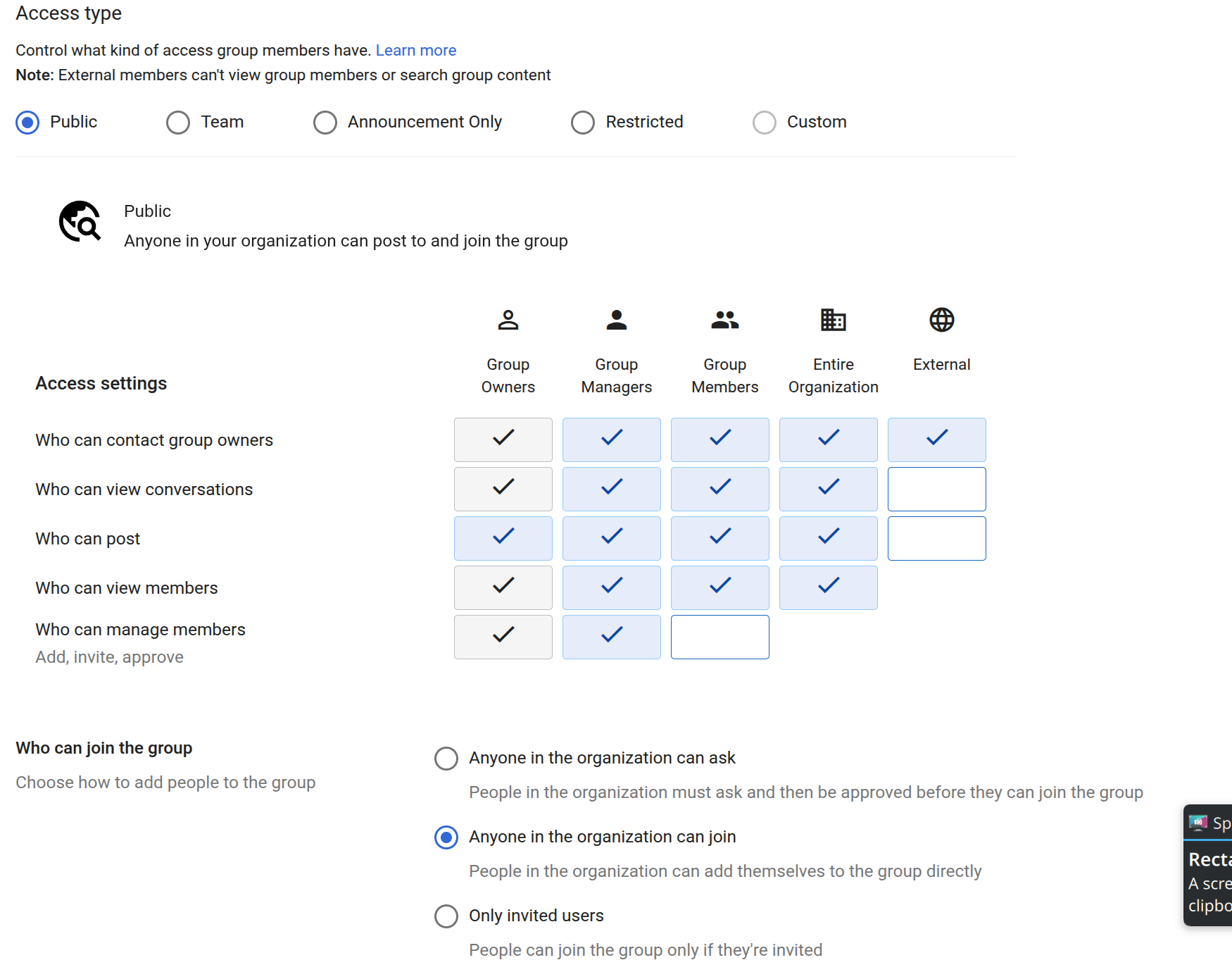
This is because for any sensible configuration of Google Groups when using it for email groups you have to use the "Custom" permissions mode. The default Public mode doesn't allow external people to email the group, but does allow the whole company to see all the messages. The default Team mode, has the same problem of everyone being able to see all the messages.
Also let's not forget that dangerous little "Anyone in the organisation can join" toggle at the bottom which is on by default. So any random new starter can join your confidential company directors group and get all the emails sent to it.
Giving Google the benefit of the doubt here, I think the reasoning might be that Google Groups is intended as a kind of company forum, not for private email groups. However that isn't how anyone uses it in my experience...