Search results for tag #networking
Okay, so let me tell you about my doorbell, from a #networking perspective.
When you push the button by the door, it sends a message over the #zigbee wireless mesh network in my house. It probably goes through a few hops, getting relayed along the way by the various Zigbee light switches and "smart outlets" I have.
Once it makes it to my utility closet, it's received by a Zigbee-to-USB dongle, through a USB hub (a simple tree network) plugged into an SFF PC. From there, it gets fed into zigbee2mqtt, which, as the name implies, publishes it to my local #mqtt broker.
The mqtt broker is in the small #kubernetes cluster of #raspberrypi nodes I run in my utility closet. To get in (via a couple of #ethernet switch hops), it goes through #metallb, which is basically a proxy-ARP type service that advertises the IP address for the mqtt endpoint to the rest of my network, then passes the traffic to the appropriate container via a #linux veth device.
I have #HomeAssistant, running in the same Kubernetes cluster, subscribed to these events. Within Kubernetes, the message goes through the CNI plugin that I use, #flannel. If the message has to pass between hosts, Flannel encapsulates it in VXLAN, so that it can be directed to the correct veth on the destination host.
Because I like #NodeRed for automation tasks more than HomeAssistant, your press of the doorbell takes another hop within the Kubernetes cluster (via a REST call) so that NodeRed can decide whether it's within the time of day I want the doorbell to ring, etc. If we're all good, NodeRed publishes an mqtt message (more VXLANs, veths, etc.)
(Oh and it also sends a notification to my phone, which means another trip through the HomeAssistant container, and leaving my home network involves another soup of acronyms including VLANs, PoE, QoS, PPPoE, NAT or IPv6, DoH, and GPON. And maybe it goes over 5G depending on where my phone is.)
Of course something's got to actually make the "ding dong" sound, and that's another Raspberry Pi that sits on top of my grandmother clock. So to get *there* the message hops through a couple Ethernet switches and my home WiFi, where it gets received by a little custom daemon I wrote that plays the sound via an attached #HiFiBerry board. Oh but wait! We're not quite done with networking, because the sound gets played through PulseAudio, which is done through a UNIX domain socket.
SO ANYWAY, that's why my doorbell rarely works and why you've been standing outside in the snow for five minutes.
Internet exchange points are critical, but ignored
https://www.theregister.com/2025/07/31/ixp_resilience_call/
Call for testing: Improved 802.11g AP compatibility check https://www.undeadly.org/cgi?action=article;sid=20250731111632 #openbsd #wifi #80211 #wireless #networking #callfortesting #freesoftware #libresoftware
Yes, The Book of PF, 4th Edition Is Coming Soon https://nxdomain.no/~peter/yes_the_book_of_pf_4th_ed_is_coming.html (also tracked https://bsdly.blogspot.com/2025/07/yes-book-of-pf-4th-edition-is-coming.html) #openbsd #freebsd #bookofpf #pf #packetfilter #book #networking #security #freesoftware #libresoftware #shamelessplug
 boosted
boostedI have a very weird issue with my #tailscale + #mumble server setup:
I have a murmur (mumble) server that binds to the tailscale interface on my server.
I have shared that endpoint with a friend and we're both connecting via tailscale to that mumble server to talk.
Every few minutes (3, 5, something like that), one of us gets reconnected. Mumble (client) says "Server failed to respond to TCP ping". On the server it says (murmur log): "Connection closed: The remote host closed the connection".
The tailscale log on the server says something like "adding connection to derp-* for ..." at that very moment of reconnecting.
How to debug this issue? I don't even know where to start. It looks like (to me, as a networking noob) that tailscale reconfigures connections and breaks the mumble connection.
#followerpower #linuxadmin #NetworkEngineering #networking #sysadmin
CC @tailscale
Please boost 
This may sound like a dumb question, but with IPv6 am I supposed to ... learn the addresses like I have for IPv4?
With IPv4 I feel as if I have had a reasonable chance of learning some of the important blocks, but with IPv6... I genuinely hesitate to "adopt" because I fear having to learn the new addressing scheme.
If not, how should I ... "think" about IPv6 coming from the perspective of actually knowing IPv4-addresses?
We are still working on The Book of PF, 4th ed.
Preorders are open at https://nostarch.com/book-of-pf-4th-edition, read about the work at https://nxdomain.no/~peter/yes_the_book_of_pf_4th_ed_is_coming.html (also tracked at https://bsdly.blogspot.com/2025/07/yes-book-of-pf-4th-edition-is-coming.html) #bookofpf #newedition #freebsdd #openbsd #pf #packetfilter #networking #security #freesoftware #libresoftware
At EuroBSDCon 2025 in Zagreb: "Network Management with the OpenBSD Packet Filter Toolset" by Peter N. M. Hansteen, Tom Smyth, Max Stucchi, see https://events.eurobsdcon.org/2025/talk/FW39CX/
Schedule at https://events.eurobsdcon.org/2025/schedule/
To register https://2025.eurobsdcon.org/registration.html
#eurobsdcon #freebsd #openbsd #networking #packetfilter #pf #security #devops #sysadmin
oh, my "Yes, The Book of PF, 4th Edition Is Coming Soon" blog post https://bsdly.blogspot.com/2025/07/yes-book-of-pf-4th-edition-is-coming.html is on hackernews: https://news.ycombinator.com/item?id=44657803 #bookofpf #pf #packetfilter #openbsd #freebsd #networking (non-tracked: https://nxdomain.no/~peter/yes_the_book_of_pf_4th_ed_is_coming.html)
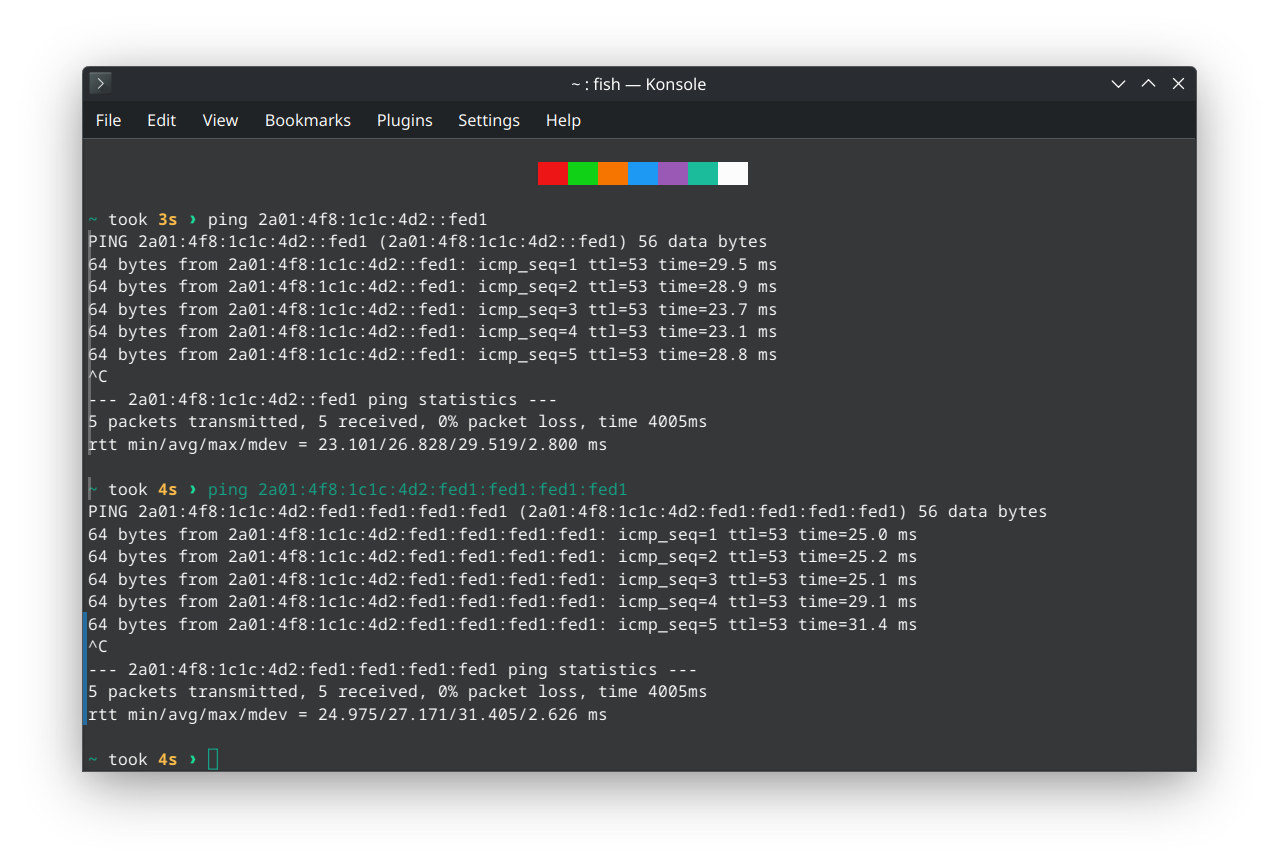
Fun-Fact: Our Mastodon instance "burningboard.net" doesn't just have the IPv6 address 2a01:4f8:1c1c:4d2::1 but is also reachable via 2a01:4f8:1c1c:4d2::fed1
as well as
2a01:4f8:1c1c:4d2:fed1:fed1:fed1:fed1
Might not make much sense, but it's funny :)
Today, early access reader feedback for The Book of PF, 4th edition proved to me that early access is worth doing.
Get yours at https://nostarch.com/book-of-pf-4th-edition, or read about the work at https://nxdomain.no/~peter/yes_the_book_of_pf_4th_ed_is_coming.html #bookofpf #newedition #freebsdd #openbsd #pf #packetfilter #networking #security #freesoftware #libresoftware
Fellow network nerds, at EuroBSDcon 2025 in Zagreb, there will be a Network Management with the OpenBSD Packet Filter Toolset" https://events.eurobsdcon.org/2025/talk/FW39CX/ session, a full day tutorial starting at 2025-09-25 10:30 CET. You can register for the conference and tutorial by following the links from the conference Registration and Prices https://2025.eurobsdcon.org/registration.html page. #openbsd #freebsd #networking #security #eurobsdcon #conference #pf #packetfilter #freesoftware #libresoftware #zagreb
@socketwench ah right - so where I left mDNS I was working out how to write nftables rules that would force any outbound traffic back to localhost to the systemd-resolved stub, which I could THEN enforce prioritizing mDNS responses, but also mDNS isn't kindof a closed and done thing like DNS is, it can just kinda, hang open for a but waiting for replies to the broadcast, and slowing everything down.
...yea I didn't get as far as investigating mDNS caching before this smelled awful
So excited about getting my new home firewall/router:
TLSense N100L4: 4x 2.5Gbit LAN, N100 CPU, 256GB NVMe SSD, 16GB RAM.
It will be running OPNSense and I'm really looking forward replacing all these horrible ASUS Routers that I've insisted on running.
Anyone here have experience with connecting a Mellanox Connect X3 network card to a Mikrotik RB3011 router?
I managed to flash the ethernet firmware unto the card, and ethtool sees is correctly:
root@cold-backup:~# ethtool enp1s0
Settings for enp1s0:
Supported ports: [ FIBRE ]
Supported link modes:
1000baseX/Full
10000baseCR/Full
10000baseSR/Full
Supported pause frame use: Symmetric Receive-only
Supports auto-negotiation: No
Supported FEC modes: Not reported
Advertised link modes:
1000baseX/Full
10000baseCR/Full
10000baseSR/Full
Advertised pause frame use: Symmetric
Advertised auto-negotiation: No
Advertised FEC modes: Not reported
Speed: Unknown!
Duplex: Unknown! (255)
Auto-negotiation: off
Port: FIBRE
PHYAD: 0
Transceiver: internal
Supports Wake-on: d
Wake-on: d
Current message level: 0x00000014 (20)
link ifdown
Link detected: no
And I tried three different cables, one optical and two DACs, and neither of them is working.
On the other side there is my Mikrotik RB3011, which also does not see any connection on the SFP port.
Yes, The Book of PF, 4th Edition Is Coming Soon https://nxdomain.no/~peter/yes_the_book_of_pf_4th_ed_is_coming.html
Long rumored and eagerly anticipated by some, the fourth edition of The Book of PF is now available for preorder https://nostarch.com/book-of-pf-4th-edition #openbsd #pf #packetfilter #freebsd #networking #security #tcpip #ipv6 #ipv4 #bookofpf
Good morning!
Tonight it is #NetMCR (https://www.netmcr.uk/) again in #Manchester.
Join them for a #Networking #MeetUp at the Northern Monk (https://www.northernmonk.com/pages/manchester) from 7pm.
Talks will include:
* *Sam Cater, 'CHERI - Bolstering security by baking it into silicon'*:
A quick run-down of what the CHERI Alliance is and how it came to be, what the technology does, how it's being utilised today with wins & losses. There will be some use-cases demonstrated and a little spin on how that's useful to Sam's employer.
* *Christian Farrow, 'From networked clocks to TikTok: atomic timekeeping makes its retro return!'*:
Our resident Time Lord is back once again with a neat run down on atomic timekeeping. Arcane mysteries or run-of-the-mill devices? Come find out!
*You?*:
Feel free to come and speak to us if you've something to speak about, on the evening or ahead of time!
Hopefully see you there for some 🍻 , 🍔, 🍟 and ℹ️ 😀
Long rumored, eagerly anticipated by some, you can now PREORDER "The Book of PF, 4th edition" https://nostarch.com/book-of-pf-4th-edition for the most up to date guide to the OpenBSD and FreeBSD networking toolset #openbsd #freebsd #networking #pf #packetfilter #firewall #preorder #security
The #mikrotik replacement switch is now in place. UI took a little time to get used to, but wasn't a huge deal. Fan is audible with the current temperatures in my office but at least it doesn't sound like I'll be picking shrapnel out of the walls any second. Plus, I do have the Noctua fan that a lot of people put into these.
So far, so good. Yes, the #Ubiquiti unified UI across all devices is nice, but I don't play with the configuration of my home network often enough for it to make a massive difference.
TIL about MAC address records in DNS.
I was thinking "man, WoL converting IPs to MACs is unsolvable given ND/ARP cache TTLs and powered-off machines". Guess it's another one we stuff in the garbage can that is DNS 😹







![[?]](https://fedi.stfn.pl/fileserver/01G5XZFT0AR1QB07GENYDDY6FT/attachment/original/01JFSF3HAPH9EBKGF13FDJPS97.jpeg)
